📝 Writing – Blocky Linux
🧪Procedure
1 -> To keep everything organized, the first thing you should always do is create a folder in your work environment with the name of the machine.
Once you’ve created it, go to the folder and run the [[mkt]] command.
Now we check the connection to the victim machine.
ping -c4 ipTarget
Now we look at the TTL to see if we’re using a Windows or Linux machine.
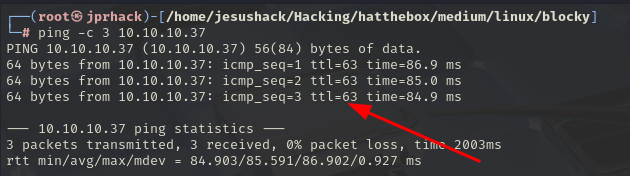
We see that it has TTL 63, so it is a Linux machine.
1️⃣ Enumeration
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn ipTarget -oG all ports
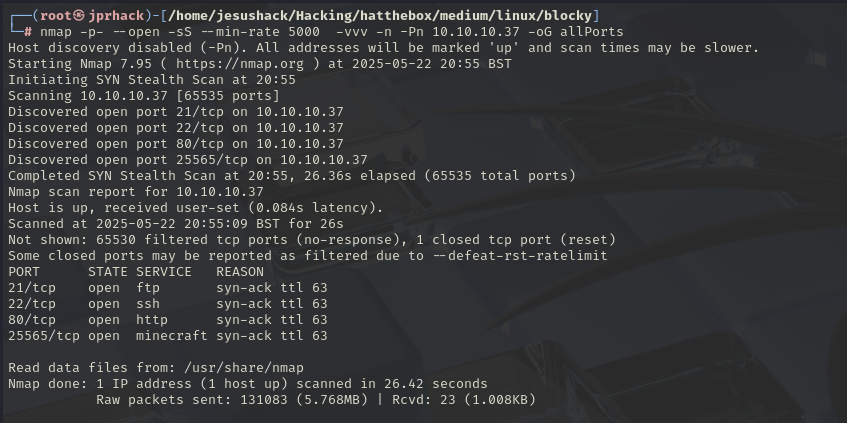
Once we have it We will extract all the ports by running the command [[extactPorts]] in the allPorts file.
extractPorts allPorts
Once we have the ports, we run
nmap -p21,22,80,25565 -sCV 10.10.10.37 -oN targeted.rb
While we have port 80 open, let’s see what we have there.
In a new window, we launch a whtaweb to see what we find.
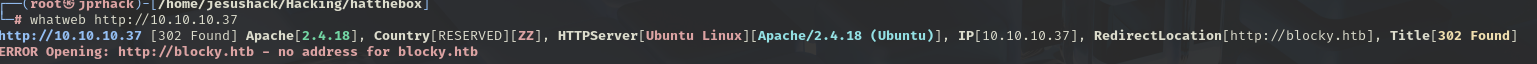
We have a 302 address and see the domain blocky.htb .
Let’s save it to our /etc/hosts file.
Now we run a whatweb again at http://blocky.htb to see what information it reports.
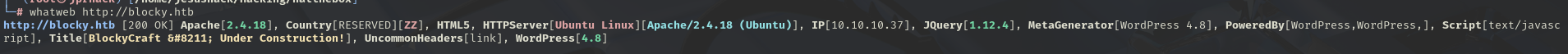
We see that it is WordPress 4.8.
If we go to the browser, we can check it with Wappalyzer.
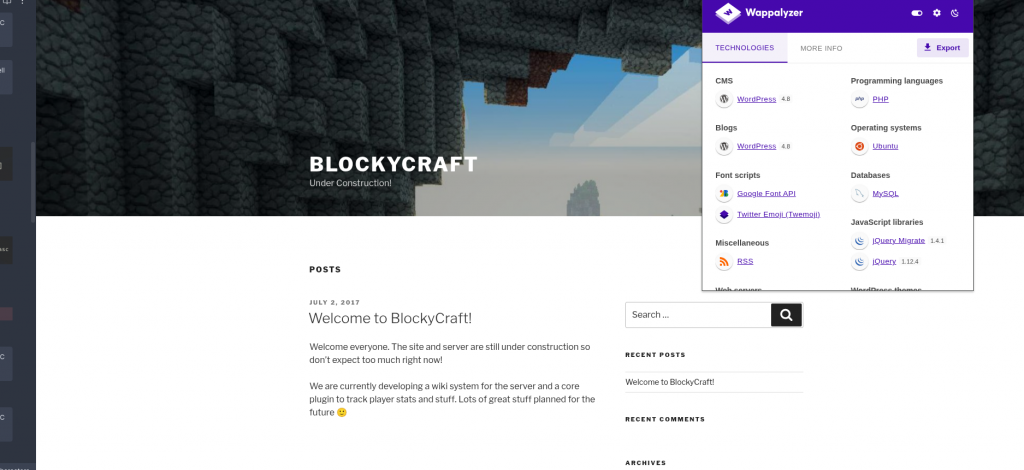
Given our first glimpse of what’s on port 80, we can see our exhaustive scan is now complete. 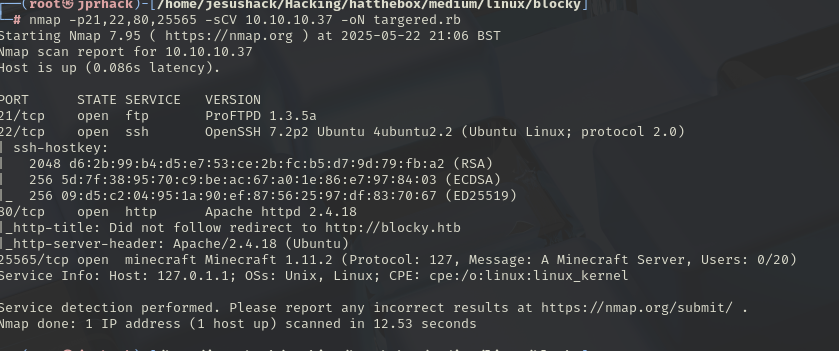
We have quite a bit of relevant information, such as the FTP version, SSH, and a Minecraft server on port 25565. Very interesting! However, we need to maintain order, so let’s list FTP port 21 first to see if we find anything of value, and so on.
FTP enumeration
┌──(root㉿jprhack)-[/home/jesushack/Hacking/hatthebox/medium/linux/blocky]
└─# ftp 10.10.10.37
Connected to 10.10.10.37.
220 ProFTPD 1.3.5a Server (Debian) [::ffff:10.10.10.37]
Name (10.10.10.37:jesushack): anonymous
331 Password required for anonymous
Password:
530 Login incorrect.
ftp: Login failed
ftp> ls
530 Please login with USER and PASS
530 Please login with USER and PASS
ftp: Can't bind for data connection: Address already in use
We do not have access as an anonymous user.
We see that the SSH version is less than 7.7, so it may be vulnerable to user enumeration, but in this case this is not the case.
We currently have port 80 under control, so we’ll first go to the remaining port in this case.
Enumeracion del puerto 25565 Minecraft
We see that it’s a Minecraft server with version 1.11.2.
We searched with searchsploit but have no luck.

Now it’s time to enumerate port 80.
Enumeracion del puerto 80 y WordPress
Let’s first look at the message it says.
“Welcome everyone. The site and server are still under construction, so don’t expect too much right now!
We are currently developing a wiki system for the server and a core plugin to track player stats and other stuff. Lots of great stuff planned for the future 🙂”
So, let’s not expect too much right now, since the website is under construction and they are developing a system for the server, I imagine for port 25565, but of course it’s not an http port. It could be that this platform is under a subdomain. Since we’re going to enumerate this quickly, we’re going to launch a brute-force attack with Gobuster to see if we can discover any subdomains.
We haven’t had any luck.
Before listing WordPress, let’s fuzz through directories to see if we find anything out of the ordinary.
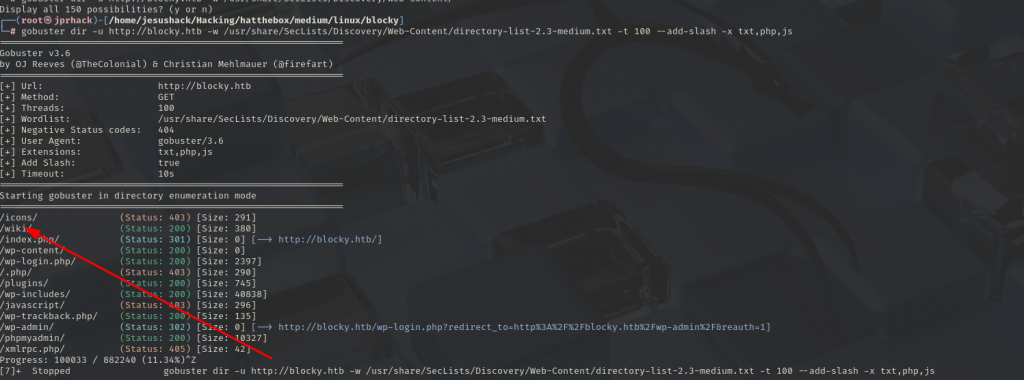
We have found a directory called wiki, this is not common in WordPress applications, let’s see what is there.
I’ve fuzzed and there’s nothing interesting.
Another interesting thing is the /plugins directory, since it’s not the directory where the WordPress plugins are located, which is /wp-content/plugins/.
Let’s see what’s there.
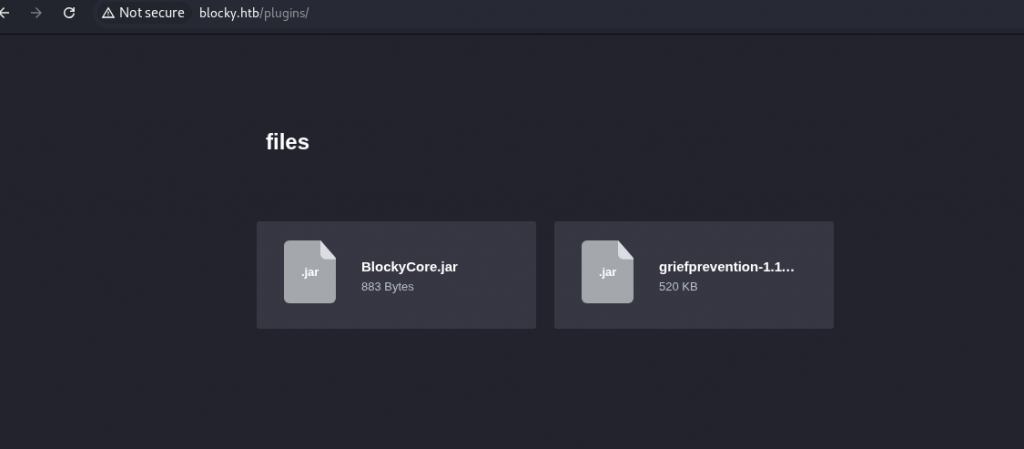
Let’s download and unzip these files.
I’m focusing on BlockyCore.jar
Inside there’s a file called BlockyCore.class
We can make
strings BlockyCore.class
Or to see the information more clearly, we can decompile the file.
wget https://www.benf.org/other/cfr/cfr-0.152.jar
java -jar cfr-0.152.jar BlockyCore.class
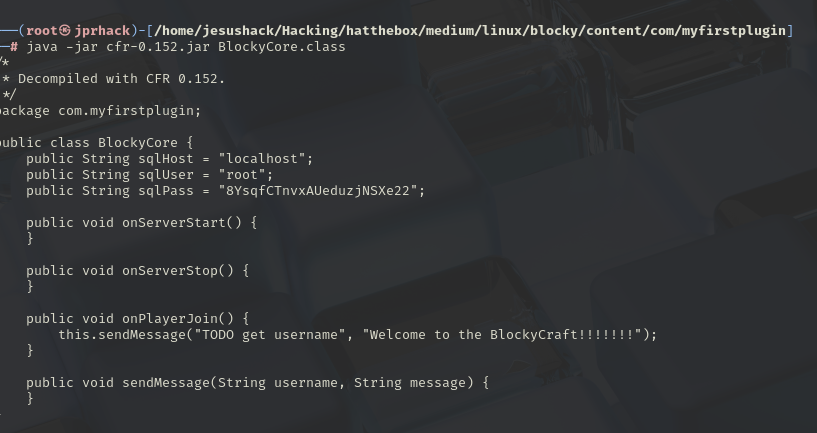
We see some database connection credentials, and we’ve seen the /phpmyadmin application, so let’s test them and see that we have access.
We see the username and password encrypted in the notch:$P$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/ database. This password isn’t the one we found, since I went to the login panel and wasn’t successful when trying to use it as a password reuse with the notch user.
Let’s test with this username and the reusable password to see if we can log in via SSH or FTP.
And indeed, we have SSH access.
Privilege Escalation
There’s nothing wrong with privilege escalation; we can become root without providing a password.
sudo su
You might also be interested in Writeup venom