Domain takeover means registering a non-existent domain name to gain control of another domain.
If attackers find an expired domain (here’s how to find them [8 – Finding Expired Domains]), they can hijack that domain to carry out other attacks, such as hosting malicious content on a website or sending a phishing email using the claimed domain.
Domain takeover is also possible with subdomains called subdomain takeovers.
A DNS canonical CNAME record is used to map different domains to a single parent domain.
Many organizations use third-party services such as AWS, GitHub, Akamai, Fastly, and other content delivery networks (CDNs) to host their content.
In this case, they typically create a subdomain and point it to those services.
For example,
sub.target.com. 60 IN CNAME anotherdomain.com
The domain name (e.g., sub.target.com) uses a CNAME record for another domain (e.g., anotherdomain.com).
Suppose the anotherdomain.com expires and is available for anyone to claim, since the target.com DNS server holds the CNAME record.
In that case, anyone who registers anotherdomain.com will have full control over the sub.target.com domain until the DNS record is updated.
We can also perform a typosquatting attack.
If the expired anotherdomain.com is not present, we can obtain a very similar domain, anotherdomain.com (here we add two nns).
Subdomain Enumeration
In addition to the other subdomain enumeration techniques, we can do the following.
Before performing a subdomain takeover, we must enumerate the subdomains of a target domain using tools such as Subfinder.
This tool can extract subdomains from open sources such as DNSdumpster.
Other tools such as Sublist3r can also be used to brute-force subdomain extraction by providing a pre-generated wordlist:
[!bash!]# ./subfinder -d inlanefreight.com -v
_ __ _ _
____ _| |__ / _(_)_ _ __| |___ _ _
(_-< || | '_ \ _| | ' \/ _ / -_) '_|
/__/\_,_|_.__/_| |_|_||_\__,_\___|_| v2.4.5
projectdiscovery.io
[WRN] Use with caution. You are responsible for your actions.
[WRN] Developers assume no liability and are not responsible for any misuse or damage.
[WRN] By using subfinder, you also agree to the terms of the APIs used.
[INF] Enumerating subdomains for inlanefreight.com
[alienvault] www.inlanefreight.com
[dnsdumpster] ns1.inlanefreight.com
[dnsdumpster] ns2.inlanefreight.com
...snip...
[bufferover] Source took 2.193235338s for enumeration
ns2.inlanefreight.com
www.inlanefreight.com
ns1.inlanefreight.com
support.inlanefreight.com
[INF] Found 4 subdomains for inlanefreight.com in 20 seconds 11 milliseconds
A great alternative is a tool called Subbrute.
This tool allows us to use self-defined resolvers and perform pure DNS brute-force attacks during internal penetration testing on hosts that don’t have internet access.
[!bash!]$ git clone https://github.com/TheRook/subbrute.git >> /dev/null 2>&1
[!bash!]$ cd subbrute
[!bash!]$ echo "ns1.inlanefreight.com" > ./resolvers.txt
[!bash!]$ ./subbrute inlanefreight.com -s ./names.txt -r ./resolvers.txt
Warning: Fewer than 16 resolvers per process, consider adding more nameservers to resolvers.txt.
inlanefreight.com
ns2.inlanefreight.com
www.inlanefreight.com
ms1.inlanefreight.com
support.inlanefreight.com
<SNIP>
Sometimes internal physical configurations are poorly protected, which we can take advantage of by uploading our tools from a USB flash drive. Another scenario would be if we reached an internal host through pivoting and wanted to work from there. Of course, there are other alternatives, but it doesn’t hurt to know alternative ways and possibilities.
The tool has found four subdomains associated with inlanefreight.com. Using the nslookup or host command, we can list the CNAME records for those subdomains.
[!bash!]# host support.inlanefreight.com
support.inlanefreight.com is an alias for inlanefreight.s3.amazonaws.com
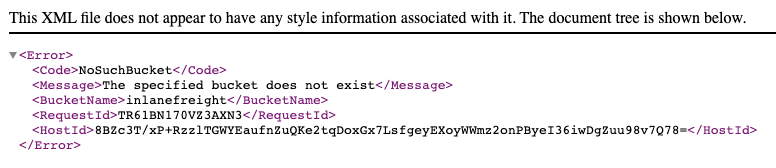
The support subdomain has an alias record pointing to an AWS S3 bucket.
However, the URL https://support.inlanefreight.com displays a NoSuchBucket error indicating that the subdomain is potentially vulnerable to a subdomain takeover.
Now, we can take over the subdomain by creating an AWS S3 bucket with the same subdomain name.
The can-i-take-over-xyz repository is also an excellent reference for a subdomain takeover vulnerability. It shows whether target services are vulnerable to a subdomain takeover and provides guidelines for assessing the vulnerability.
This information is part of my academy notes https://academy.hackthebox.com/module/116/section/1512
